📝 Blog Summary
Is your enterprise communication really secure? The blog explores how advanced PBX encryption, SBCs, firewalls, and predictive analytics create a multi-layered defense that safeguards your Hosted PBX from unseen threats.
As cyber threats evolve, enterprise communication systems must adapt to them. AI-driven VoIP security solutions, predictive analytics, and adaptive PBX encryption strategies are shaping the future of Hosted PBX security. Today’s security isn’t just about firewalls; it’s about anticipating attacks, automatically neutralizing risks, and ensuring that communications remain seamless and invisible to users.
A holistic approach to security begins with understanding how encryption safeguards voice and video traffic, and how it integrates with other protective measures. Adopting robust PBX encryption strategies is essential not only to prevent unauthorized access but also to maintain the integrity and confidentiality of sensitive communications. Meanwhile, exploring comprehensive VoIP security solutions can provide layered defenses that proactively detect and neutralize potential vulnerabilities.
With this context in mind, let’s delve into the key strategies for implementing a fully secure Hosted PBX system, starting with encryption practices that protect the very foundation of your communications.
Did You Know?
The global hosted PBX market is expected to expand from USD 11.5 billion in 2023 to USD 24.9 billion by 2028, with a CAGR of 16.8% during this period.
How to Implement Encryption to Secure Voice and Video Traffic in a Hosted PBX?
Protecting voice and video traffic in a Hosted PBX environment is essential, as these channels often carry highly sensitive conversations. Implementing robust PBX encryption strategies ensures that signaling data, media streams, and messaging remain confidential and secure. An intelligent SBC for VoIP security enforces these policies in real-time. Key steps to secure voice and video traffic include:

- Encrypt Signaling and Media: Use TLS for signaling (call setup, routing, teardown) and SRTP for media streams. This ensures that both the control and content of calls are unreadable if intercepted.
- SBC-Based Session Validation: Deploy SBCs to authenticate calls, verify session integrity, and enforce encryption policies. This ensures that only secure sessions are allowed to traverse your network.
- Tenant-Specific Encryption: In multi-tenant setups, custom VoIP SBC development allows for tenant-specific encryption enforcement, ensuring that each client’s communications remain isolated and secure.
- Continuous Monitoring: Integrating SBC solutions for VoIP security to monitor traffic for attempts to bypass encryption or inject malicious streams, allowing proactive mitigation.
- Regular Updates and Certificate Management: Keep encryption protocols, certificates, and SBC firmware up to date to prevent vulnerabilities and maintain compliance.
By combining end-to-end encryption, SBC validation, and continuous monitoring, enterprises create a secure foundation for all communications. This layered strategy ensures that sensitive calls, video conferences, and multi-party collaborations remain confidential and tamper-proof. Implementing these measures also naturally sets the stage for broader hosted PBX security strategies, including firewalls, predictive analytics, and invisible security protections.
How Does End-to-End Encryption Protect Voice and Video Traffic in Hosted PBX?
The first step toward robust hosted PBX security is encryption. End-to-end encryption ensures that voice and video data remain unintelligible if intercepted. Protocols like TLS for signaling and SRTP for media streams are critical, but they are not a standalone solution. A sophisticated approach combines encryption with intelligent traffic management using an SBC.
This is precisely why SBC for VoIP security is indispensable in modern setups. By inspecting signaling traffic, validating call authenticity, and enforcing encryption policies, SBCs prevent eavesdropping, call spoofing, and media tampering. Encryption and SBCs together create a dynamic defense that adapts in real time to attempted breaches, ensuring communications remain secure without burdening users with manual intervention. Key benefits of end-to-end encryption include:
1. Protection Against Interception
By encrypting both signaling and media channels, all voice and video streams remain unreadable even if intercepted by malicious actors. This is critical in scenarios where confidential boardroom discussions or client negotiations are conducted remotely.
2. Call Integrity Verification
Beyond encryption, modern protocols verify the source and integrity of each call, ensuring that no unauthorized modifications occur in transit. This prevents attackers from injecting fraudulent commands or altering communication flows.
3. Compliance Support
End-to-end encryption aligns with global data privacy standards and regulations, ensuring that enterprises avoid legal repercussions while maintaining customer trust and confidence.
4. Seamless User Experience
Users experience no disruption or latency, as encryption processes occur in the background. This “invisible” layer of protection ensures operational efficiency and adoption without training overhead.
5. Integration with SBCs
When combined with a properly configured SBC for VoIP security, encrypted traffic is also validated against session policies, providing dual layers of trust and reducing potential security gaps.
With encrypted traffic safeguarded, organizations often face the challenge of multi-tenant Hosted PBX deployments, where multiple clients share the same infrastructure but demand complete data isolation.
How Can Multi-Tenant Hosted PBX Services Be Secured for Multiple Clients?
Effectively securing multi-tenant Hosted PBX environments requires a combination of advanced technical measures and continuous monitoring. Custom VoIP SBC Development plays a central role here. By designing SBCs for a multi-tenant environment, service providers can enforce tenant-specific routing rules, authentication protocols, and policy compliance. Key steps and best practices for securing multi-tenant environments include:
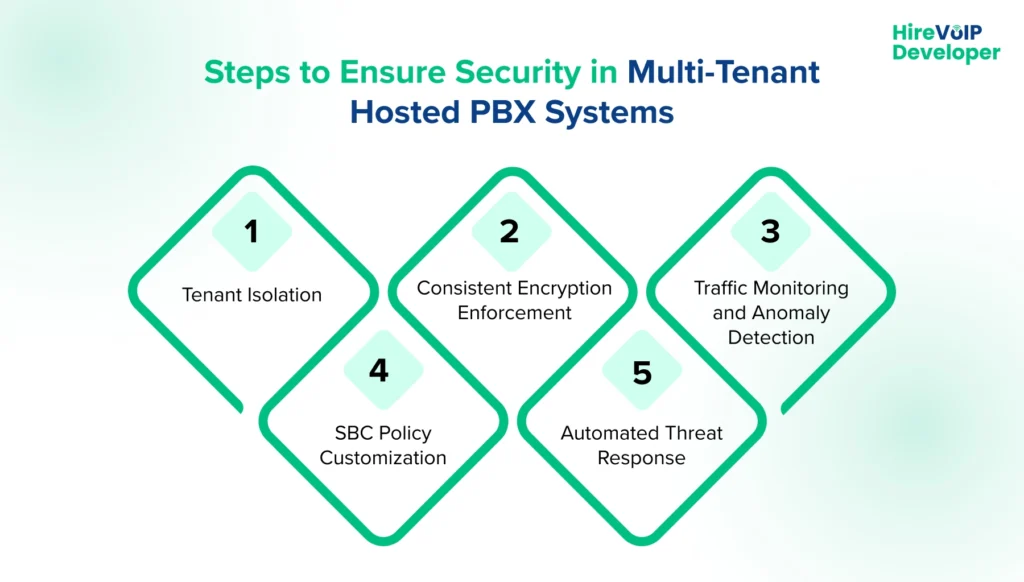
1. Tenant Isolation
Each tenant’s data and call traffic must be fully segregated using virtualized SBC sessions and VLAN segmentation. For example, one client’s internal calls should never traverse another tenant’s network, preventing accidental exposure or leakage.
2. Consistent Encryption Enforcement
Encryption policies should be applied uniformly across all tenants. This includes securing signaling with TLS and media streams with SRTP, ensuring that even if a breach occurs, the intercepted data remains unreadable.
3. Traffic Monitoring and Anomaly Detection
Continuous monitoring of call patterns, traffic volume, and endpoint behavior is critical. Predictive analytics can identify unusual patterns, such as sudden spikes in tenant call volume, which may indicate fraud or a system compromise.
4. SBC Policy Customization
Each tenant may have unique requirements, such as internal PBX extensions, international dialing rules, or compliance protocols. Customizing SBC policies per tenant ensures that routing, authentication, and call validation rules align with each client’s specific needs, thereby maintaining both functionality and security.
5. Automated Threat Response
By integrating real-time monitoring tools with the SBC and firewall, anomalies or malicious behavior can be automatically detected and mitigated. For example, if a suspicious call attempt is detected from an external endpoint, the system can quarantine that session and immediately alert administrators.
Without proper safeguards, there is a risk of cross-tenant exposure, in which another tenant could inadvertently access another client’s sensitive data. To maintain trust and ensure compliance, each tenant must have fully segregated, encrypted communication channels implemented through robust PBX encryption.
How Do Encryption, SBCs, and Firewalls Work Together to Secure Hosted PBX?
Layered security remains the most effective and widely adopted approach for ensuring the security of Hosted PBX. No single tool or protocol can defend against the wide range of threats modern VoIP systems face, including eavesdropping, call spoofing, toll fraud, and ransomware. By combining encryption, SBCs, and firewalls, enterprises establish multiple protective layers that work in concert to mitigate risks while maintaining seamless communication. Together, these components form a comprehensive VoIP security solution capable of defending against both known and emerging threats. Key aspects of layered security include:
1. Encryption at Rest and in Transit
Encryption protects voice, video, and messaging streams by converting data into unreadable formats. TLS ensures that signaling information, such as call setup and teardown, cannot be intercepted or modified, while SRTP encrypts the media itself. Even if someone infiltrates the network, the content remains protected. This dual-layer encryption ensures privacy for internal conversations, client meetings, and sensitive negotiations.
2. SBC Authentication and Validation
Session Border Controllers act as intelligent gatekeepers. They authenticate the origin of each call, verify that it complies with predefined policies, and ensure that only legitimate sessions are allowed to traverse the network. For example, an SBC can detect and block a spoofed caller ID or prevent calls from unregistered devices, effectively reducing the risk of fraud or unauthorized access. The precision offered by SBC for VoIP security ensures that all communications are verified before reaching the end user.
3. Firewall Perimeter Protection
Firewalls form the first line of defense by regulating network traffic both inbound and outbound.. Advanced firewall rules can filter VoIP-specific protocols, block suspicious IP addresses, and isolate network segments from unauthorized access. When integrated with SBCs, firewalls not only filter malicious traffic but also complement internal call validation and encryption policies, creating a tightly controlled environment for Hosted PBX systems.
4. Integrated Threat Detection
Modern VoIP security solutions provide continuous monitoring of network traffic and call patterns. This integration enables real-time detection of anomalies, including unusual call volumes, repeated failed authentication attempts, and abnormal session behavior. Automated systems can immediately flag these events, quarantine affected sessions, or alert administrators for rapid mitigation, ensuring that threats are neutralized before they escalate.
5. Expert Oversight and Configuration
Even with robust tools in place, human expertise remains critical. Organizations that hire SBC developers benefit from specialized knowledge in optimizing configurations for multi-tenant environments, fine-tuning encryption protocols, and ensuring that layered security mechanisms function seamlessly together. Expert oversight guarantees that all security layers are consistently applied, minimizing gaps and enhancing the resilience of Hosted PBX deployments.
With these foundational measures in place, proactive security strategies become the next focus, enabling organizations to identify vulnerabilities before they escalate and become more severe.
Did You Know?
The global Session Border Controllers market is expected to expand considerably, rising from USD 838.0 million in 2025 to USD 1,886.0 million by 2035, reflecting a robust CAGR of 8.2%.
How Can Predictive Analytics Identify Security Vulnerabilities in Hosted PBX Before an Attack?
In modern Hosted PBX security, predictive analytics has emerged as a vital tool for preemptively identifying and mitigating threats. Unlike traditional reactive approaches that respond after an incident occurs, predictive analytics leverages historical and real-time data to forecast potential security breaches. Key functions of predictive analytics include:
1. Anomaly Detection
Predictive systems continuously monitor call volumes, duration, and patterns to identify anomalies. Sudden spikes in outbound calls, frequent failed login attempts, or unusual call routing may indicate fraud attempts, toll fraud, or compromised endpoints. For example, a sudden surge in international calls from a previously dormant extension can trigger an alert for further investigation.
2. Risk Scoring
Every user, device, and network segment can be assigned a dynamic risk score based on historical behavior, access privileges, and recent activity. Higher risk scores can automatically trigger stricter verification measures, temporary session suspension, or additional encryption requirements, ensuring that potential threats are contained before they impact operations.
3. Automated Alerts
Predictive analytics systems generate real-time alerts to administrators when suspicious activity is detected. These alerts can include detailed context such as affected endpoints, call metadata, and potential threat vectors, enabling rapid response without waiting for manual monitoring.
4. Integration with SBCs
When integrated with SBC for VoIP security, predictive analytics can automatically validate flagged calls or sessions. This ensures that suspicious activity is blocked at the session level, preventing unauthorized access and maintaining the integrity of ongoing communications. For instance, if a predictive system identifies a call from an unregistered device exhibiting abnormal behavior, the SBC can quarantine the session while alerting the administrator.
5. Dynamic Firewall Adjustment
Predictive insights can be directly fed into firewall configurations, enabling rules to adapt in real-time. If anomalous traffic patterns are detected, the firewall can automatically block specific IP ranges, adjust protocol permissions, or isolate network segments. This adaptive capability ensures that threats are mitigated instantly without affecting legitimate traffic.
When combined with robust PBX encryption strategies, predictive analytics ensures that intercepted communications remain unreadable and uninterpretable. This proactive stance ensures the Hosted PBX environment remains secure, resilient, and user-transparent, paving the way for invisible security practices.
How Can Invisible Security Be Implemented Without Disrupting Hosted PBX Users?
Invisible security enables protective mechanisms to operate quietly in the background without impacting user workflows. Employees can conduct calls, video conferences, and messaging seamlessly while the system secures every interaction.
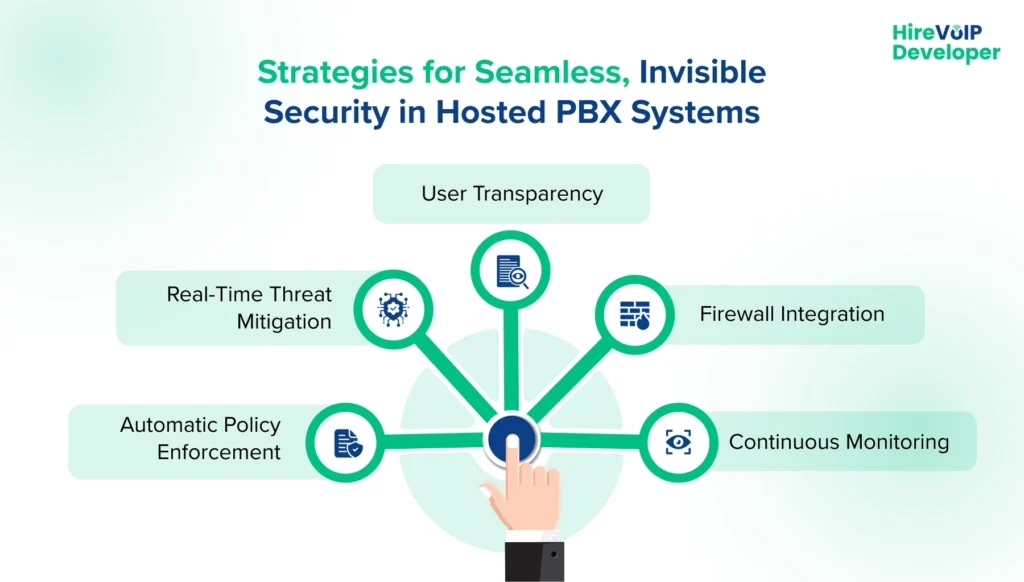
Key components of invisible security:
- Automatic Policy Enforcement: SBCs apply encryption and authentication without user input.
- Real-Time Threat Mitigation: VoIP security solutions detect and neutralize threats in real-time.
- User Transparency: Security operates without slowing down calls or creating interruptions.
- Firewall Integration: Dynamic rules adjust silently based on traffic behavior.
- Continuous Monitoring: Predictive analytics enable the detection of threats before they impact operations.
This approach ensures ongoing Hosted PBX security while maintaining an uninterrupted user experience.
How Can Long-Term Maintenance Ensure Hosted PBX Security Remains Effective?
Security is a continuous effort. Maintaining long-term Hosted PBX security requires regular monitoring, protocol updates, and ongoing system optimization to ensure optimal performance and security. Encryption protocols must evolve to counter emerging threats, SBC configurations need fine-tuning, and firewall policies must adjust dynamically to changing traffic patterns.
Best practices for long-term maintenance:
- Regular Protocol Updates: Keep TLS, SRTP, and other encryption protocols up to date.
- SBC Policy Review: Continuously audit and refine call routing and authentication policy.
- Firewall Optimization: Adjust rules based on traffic trends and emerging attack vectors to enhance security and prevent potential threats.
- Predictive Analytics Integration: Ensure that real-time threat detection remains effective and efficient.
- Expert Oversight: Organizations that hire experienced SBC Developers benefit from advanced monitoring and configuration adjustments.
By aligning advanced technology with trusted expertise, enterprises can ensure their Hosted PBX systems remain not just secure for today, but resilient against the challenges of tomorrow.
How Can Enterprises Future-Proof Hosted PBX Security?
The landscape of communication threats is evolving at an unprecedented pace. Hackers continually devise new techniques to exploit vulnerabilities in voice, video, and messaging platforms, making future-proofing a critical aspect of Hosted PBX security. A reactive approach, fixing issues after they occur, is no longer sufficient. Enterprises need a proactive, multi-layered strategy that combines PBX encryption strategies, SBC deployment, firewall protections, and advanced VoIP security solutions to defend against both current and emerging threats.
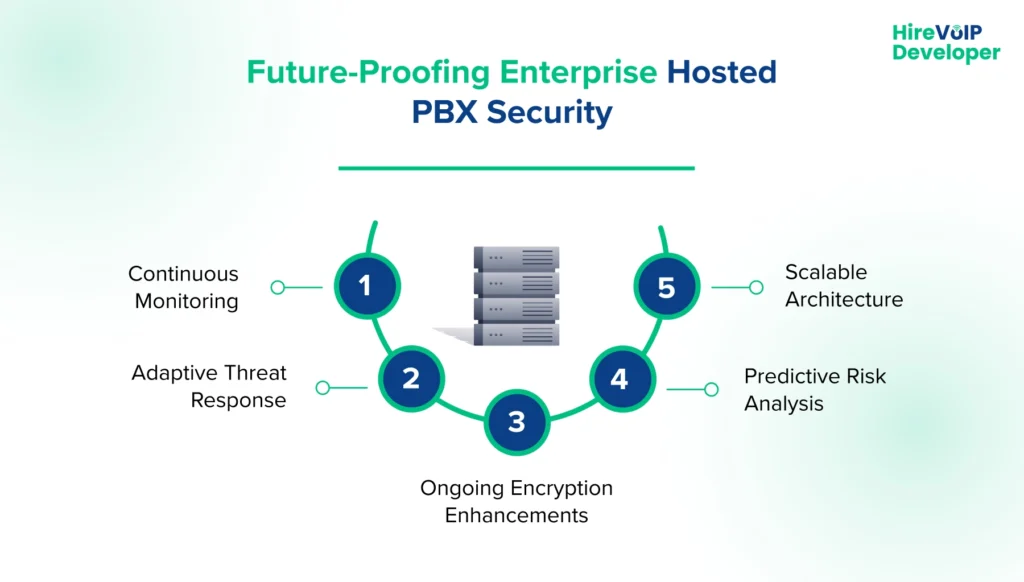
Key steps to future-proof Hosted PBX security include:
1. Continuous Monitoring
Maintaining comprehensive visibility across all voice, video, and messaging traffic is foundational. Real-time monitoring detects deviations in call patterns, abnormal endpoint behavior, or unusual network activity. For instance, an unexpected surge in international calls can be flagged instantly, triggering automated checks via SBCs and firewalls to prevent potential fraud.
2. Adaptive Threat Response
Integrating AI-driven VoIP security solutions allows systems to learn from past attacks, adapt to new threats, and respond automatically. This includes dynamic blocking of suspicious IP addresses, quarantining anomalous calls, and adjusting routing policies without manual intervention, ensuring threats are neutralized before they affect end users.
3. Ongoing Encryption Enhancements
Cyber threats evolve constantly, rendering outdated protocols vulnerable. Upgrading encryption mechanisms for signaling and media traffic, such as TLS and SRTP, ensures that even if attackers intercept network traffic, they cannot decipher sensitive communications. Pairing encryption with SBC for VoIP security ensures that these updates are applied consistently across all tenants and sessions.
4. Predictive Risk Analysis
Using advanced analytics, organizations can forecast potential vulnerabilities before they are exploited. By combining behavioral analysis, call patterns, and network metrics, predictive systems assign risk scores, detect anomalies early, and integrate with SBCs to prevent unauthorized access. This proactive insight is crucial for multi-tenant environments, where client isolation and data integrity are of paramount importance.
5. Scalable Architecture
A future-proof Hosted PBX environment must be able to grow with the organization. SBCs, firewalls, and monitoring tools should be designed to handle increasing traffic volumes, new tenants, and expanding communication channels. Scalability ensures that security measures remain effective even as the infrastructure grows, without compromising performance or reliability.
By adopting this comprehensive strategy, every voice call, video conference, and message remains protected.
In a Nutshell
Securing Hosted PBX systems is not a one-time effort; it requires an ongoing, multi-layered approach. Integrating PBX encryption strategies, SBC deployment, firewalls, and advanced VoIP security solutions ensures communications remain private, resilient, and scalable. Predictive analytics and invisible security practices further strengthen the system, providing proactive defense without disrupting workflows.
If your organization is looking to enhance its defenses or customize multi-tenant environments, the specialists at Hire VoIP Developer can help. With deep experience in SBC development, encryption deployment, and end-to-end Hosted PBX security, our team delivers scalable, future-proof solutions tailored to your business.
Secure your communications today with a partner that understands the complexity of modern VoIP environments. Choose Hire VoIP Developer. Reach out today!


