📝 Quick Summary
Securing SIP isn’t about adding more tools, it’s about knowing where control actually belongs, and we’ve covered it all. From the SIP threats providers run into every day, to the OpenSIPS modules that quietly handle them, to how those controls fit into a real security stack, this guide shows where SIP security actually breaks, and how to fix it before it becomes a problem.
Most SIP security issues don’t start as “attacks.”
They start as edge cases: a misbehaving client, an aggressive retry loop, an unexpected traffic spike, or an exposed header that shouldn’t be there. And for VoIP providers, it’s usually these small gaps that snowball into outages, abuse, or unwanted exposure.
That’s why SIP security goes beyond firewalls and TLS. It’s about what happens within the signaling flow, how behavior is controlled, how much information leaks, and how early abnormal patterns are detected.
OpenSIPS implements this with purpose-built modules, each guarding a specific part of the flow. This guide is written for VoIP providers and teams running production SIP infrastructure and focuses on the modules that make a real difference in real deployments.
We’ll walk through seven OpenSIPS modules, explain why each one matters, and show how they’re used in practice, so you can identify where the gaps usually occur and how to close them without overcomplicating your setup.
What Are the Threats to SIP Security?
Before we look at how OpenSIPS modules help protect your system, it’s important to understand what you’re defending against. SIP (Session Initiation Protocol) is the cornerstone of VoIP signaling, and because it’s widely exposed on the public internet, it attracts a predictable set of threats that exploit weaknesses in authentication, protocol behavior, and signaling logic.
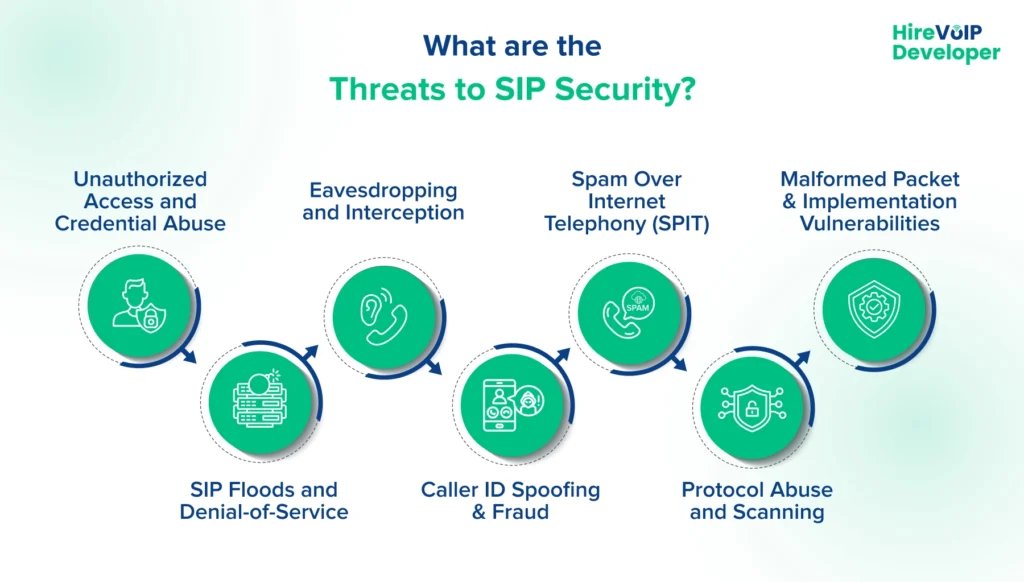
1. Unauthorized Access and Credential Abuse
Attackers often target SIP authentication mechanisms by guessing or brute-forcing usernames and passwords. If they succeed, they can register unauthorized clients, place toll calls, or otherwise abuse your system.
2. SIP Floods and Denial-of-Service
A SIP flood is a high-rate stream of spoofed SIP requests (e.g., INVITEs, REGISTERs) that overwhelms servers or back-end resources, causing legitimate calls to fail and service disruption.
3. Eavesdropping and Interception
Without proper encryption, SIP signaling and media paths can be intercepted or tampered with on the network, exposing call metadata and potentially sensitive payload data.
4. Caller ID Spoofing & Fraud
Because SIP does not natively verify caller identity, attackers can spoof caller ID information to impersonate users, execute vishing attacks, or redirect calls to premium-rate numbers. In regulated industries, these risks extend beyond fraud and reputation to potential regulatory compliance (HIPAA, GDPR….) violations.
5. Spam Over Internet Telephony (SPIT)
Just as email can be spammed, SIP endpoints can be inundated with unsolicited calls generated automatically. SPIT clogs systems and degrades service quality for legitimate users.
6. Protocol Abuse and Scanning
Attackers systematically scan SIP infrastructure to discover open ports, enumerate valid usernames or extensions, and probe for misconfigurations that can be exploited in follow-on attacks.
7. Malformed Packet & Implementation Vulnerabilities
Certain malformed SIP requests, such as improperly constructed INVITEs, can crash SIP stacks or force undefined behavior in poorly hardened implementations, issues that often surface when teams haven’t mastered how the SIP stack behaves under edge cases and protocol abuse.
Why do these matter to VoIP providers?
These threats operate at the signaling layer itself and can impact call setup, platform availability, billing, and customer experience, often before any “higher” security alert triggers. Understanding these risks helps you appreciate why the right OpenSIPS modules matter, since they enforce controls inside the SIP flow rather than only at the network edge.
These are the kinds of issues SIP platforms face in real deployments.
The next step is understanding how OpenSIPS lets you control them directly at the signaling layer.
Below are seven OpenSIPS modules that VoIP providers use to mitigate these risks, each targeting a specific SIP security gap.
Fix SIP Security Gaps Before They Become Incidents 🚨
How VoIP Providers Use 7 OpenSIPS Modules for SIP Security?
Each module targets a specific security gap at the SIP layer, from access control and traffic abuse to topology exposure and suspicious call behavior. As you go through them, you’ll see what each module is responsible for, the types of threats it helps mitigate, and what to consider when enabling it, so you can evaluate which controls your current setup lacks and where to strengthen them.
1. auth / auth_db – SIP Authentication Control
What it does: auth and auth_db modules enforce SIP digest authentication, ensuring only valid users and devices can register or place calls.
What threat it mitigate?
- Unauthorized registrations
- Credential abuse and account takeover
- Basic toll fraud via stolen SIP credentials
Quick example:
if (!www_authorize(“example.com”, “subscriber”)) {
www_challenge(“example.com”, “0”);
exit;
}
Deployment tip & trade-offs
Authentication should be mandatory for public-facing SIP endpoints. Pair auth_db with strong password policies and rate limiting, or brute-force attempts will still hurt performance.
Testing checklist
- Attempt REGISTER without credentials → expect 401
- Attempt REGISTER with wrong credentials → expect challenge
- Verify successful auth only for valid users
2. tls – Securing SIP Signaling Transport
What it does: Enables SIP over TLS to encrypt signaling traffic between endpoints, peers, and upstream carriers.
What threat it mitigate?
- Credential sniffing
- SIP message interception
- Man-in-the-middle attacks
Quick example:
listen = tls:1.2.3.4:5061
Deployment tip & trade-offs
TLS should be enforced on external interfaces. Expect slightly higher CPU usage and make sure certificates, cipher suites, and certificate rotation are handled properly.
Testing checklistx
- Confirm SIP traffic uses TLS (not UDP/TCP)
- Validate certificate chain and expiry
- Reject non-TLS traffic on public interfaces
3. pike – SIP Flood Detection
What it does: Monitors incoming SIP traffic patterns and detects abusive request rates from a single source.
What threat it mitigate?
- SIP floods
- Registration storms
- INVITE-based DoS attacks
Quick example:
if (pike_check_req()) {
xlog(“SIP flood detected from $si\n”);
exit;
}
Deployment tip & trade-offs
pike is most effective when paired with firewall rules or automated blocking. Poorly tuned thresholds can cause false positives during traffic spikes.
Testing checklist
- Generate high-rate SIP requests from one IP
- Verify pike triggers and logs the event
- Ensure legitimate traffic still passes
4. ratelimit – Controlling Request Abuse
What it does: Limits the rate of specific SIP request types such as REGISTER or INVITE.
What threat it mitigate?
- Credential brute forcing
- Excessive call attempts
- Application-layer DoS
Quick example:
if (url_check(“registrations”, 10)) {
send_reply(429, “Too Many Requests”);
exit;
}
Deployment tip & trade-offs
Use method-based limits instead of global caps. Overly aggressive limits can affect legitimate high-CPS customers.
Testing checklist
- Exceed configured request limits
- Verify 429 responses
- Confirm normal traffic remains unaffected
5. topology_hiding – Protecting Network Exposure
What it does: Hides internal IPs, routing logic, and SIP headers from external visibility.
What threat it mitigate?
- Network reconnaissance
- Targeted attacks on internal SIP elements
- Infrastructure exposure
Quick example:
topology_hiding();
Deployment tip & trade-offs
Critical for SBC-style deployments. Requires careful testing of dialog teardown (BYE/ACK) and failover scenarios.
Testing checklist
- Inspect SIP headers externally
- Confirm internal IPs are hidden
- Validate call teardown works correctly
6. fraud_detection – Call Behavior Monitoring
What it does: Detects abnormal call patterns based on call rate, destination, and duration.
What threat it mitigate?
- Toll fraud
- High-risk destination abuse
- Compromised account behavior
Quick example:
if (is_fraud()) {
xlog(“Fraud pattern detected\n”);
}
Deployment tip & trade-offs
Threshold tuning is essential. Too strict, and you’ll flag normal traffic. Too loose, and fraud slips through.
Testing checklist
- Simulate rapid calls to premium destinations
- Verify alerts or logs trigger
- Confirm legitimate traffic is not blocked
7. rtpengine / rtpproxy – Media Path Protection
What it does: Relays RTP streams and supports SRTP, NAT traversal, and media path control.
What threat it mitigate?
- Media IP leakage
- RTP interception
- Broken NAT traversal exposing endpoints
Quick example:
rtpengine_manage();
Deployment tip & trade-offs
Media relays add CPU and bandwidth load. Monitor port usage and ensure capacity planning is aligned with call volume.
Testing checklist
- Confirm RTP flows through relay
- Validate SRTP when enabled
- Ensure no direct media leaks occur
Taken together, these modules form a layered SIP security approach that helps VoIP providers reduce exposure, limit abuse, and keep signaling stable as traffic and threat patterns evolve.
But can this actually block bad traffic in real time?
Let’s see how these modules enable OpenSIPS to move beyond static rules and proactively identify and block suspicious SIP traffic in real time.
How can OpenSIPS help identify and block suspicious source IPs in real time?
OpenSIPS sits directly in the SIP signaling path, which puts it in a unique position: it doesn’t just see traffic volume, it sees behavior. Every REGISTER attempt, INVITE burst, failed authentication, malformed message, and retry loop passes through the routing logic. That visibility enables OpenSIPS to identify suspicious sources in real time and respond before issues escalate.
Using modules like pike, ratelimit, auth, and script-level counters, OpenSIPS can correlate patterns that firewalls and SBCs typically miss. A single IP that repeatedly fails authentication, spikes REGISTER requests, or sends malformed SIP messages can be flagged immediately. Once identified, OpenSIPS can take action on the spot, dropping requests, tagging traffic, triggering events, or handing the IP off to external blocking systems.
This is not post-incident analysis. It’s in-line decision-making applied at the exact moment signaling behavior deviates from normal.
Now that you’ve seen how OpenSIPS reacts to suspicious SIP behavior in real time, it’s worth revisiting an important point when I said – OpenSIPS can correlate patterns that firewalls and SBCs typically miss, “SBC typically miss!!!” So let’s see why SBC for security alone is not enough.
What security risks remain if SIP protection is handled only by SBCs?
SBCs are a critical part of any VoIP provider’s architecture, but they are not designed to be the only line of defense for SIP security. Most SBCs focus on session control, interconnection policy, and media handling. They do less to understand fine-grained SIP behavior and to react to it dynamically.
When SIP protection is handled only by SBCs, several risks tend to remain:
Limited visibility into SIP behavior
SBCs often abstract SIP logic, making it harder to track patterns such as repeated authentication failures, method-specific abuse, or malformed request sequences over time.
Coarse-grained rate limiting
While SBCs can throttle traffic, they typically lack context. They may limit volume, but they don’t easily distinguish between a legitimate traffic spike and a brute-force or scanning attempt.
Delayed or reactive blocking
Many SBC responses are threshold- or policy-driven rather than behavior-driven. Suspicious sources can remain active longer before being blocked, increasing exposure.
Less control over per-request decisions
SBCs generally operate at the session level. They don’t offer the same level of flexibility as OpenSIPS scripting for inspecting, tagging, or dropping individual SIP requests based on real-time logic.
Reduced integration with signaling-aware automation
Triggering actions like dynamic IP blocking, fraud alerts, or custom routing decisions based on SIP-level events is often limited or indirect when handled only at the SBC layer.
This doesn’t make SBCs ineffective; it highlights their role. SBCs protect the edge and manage sessions, while OpenSIPS adds a behavior-aware control layer inside the signaling path. Used together, they close gaps that neither can fully address on its own.
If SBCs define the perimeter, something still has to enforce behavior inside it, and that is where these OpenSIPS modules fit into the larger security stack.
How these modules fit into a complete security stack
OpenSIPS doesn’t replace your existing security controls, it strengthens them.
In a typical provider deployment:
- Firewalls handle coarse network-level filtering.
- OpenSIPS inspects SIP behavior in real time and decides what traffic is trustworthy.
- SBCs manage interconnects, media anchoring, and policy enforcement.
- External systems (iptables, fail2ban, SIEMs) receive signals from OpenSIPS to block or alert on bad actors.
For example, when pike or ratelimit detects abusive behavior, OpenSIPS can immediately drop requests and simultaneously trigger a firewall rule update. This creates a feedback loop where suspicious IPs are contained quickly, without waiting for manual intervention or downstream failures.
That layered approach is what keeps SIP platforms stable under unpredictable traffic conditions. But knowing how the pieces fit together is one thing, making sure they’re actually in place is another.
SIP Security Validation Checklist for VoIP Providers
Use this checklist to validate whether your OpenSIPS deployment is enforcing SIP security at the signaling layer, not just relying on perimeter controls.
Access & Authentication
✅ SIP registrations are accepted only from authenticated users or explicitly trusted peers.
✅ Repeated authentication failures are visible in logs and tied back to source IPs.
✅ Authentication checks are enforced before routing decisions are made.
Traffic Behavior & Abuse Control
✅ SIP request rates are monitored per source and per method (REGISTER, INVITE, etc.).
✅ Abnormal request patterns trigger immediate action, not just alerts.
✅ Legitimate traffic spikes are handled without blocking trusted sources.
Topology & Information Exposure
✅ Internal IPs, routing logic, and network structure are not exposed in SIP headers.
✅ External peers see only what they need to complete call signaling.
✅ Dialog teardown and failover work correctly with topology hiding enabled.
Media Path Control
✅ RTP flows are anchored where required to prevent endpoint exposure.
✅ Media paths are monitored for failures and misrouting.
✅ NAT traversal does not leak internal addresses.
Automation & Integration
✅ OpenSIPS security events can trigger external actions (firewall rules, alerts, SIEM).
✅ SIP-layer decisions are not isolated from the rest of the security stack.
✅ Blocking or throttling does not require manual intervention during incidents.
Operational Readiness
✅ Logs clearly explain why traffic was blocked or limited.
✅ Security behavior can be tested safely without impacting live traffic.
✅ Changes to SIP security rules are reviewed and documented.
With these checks in place, you should have a clear picture of where your SIP security stands and what still needs attention. That brings us to the final takeaway.
🔒 Are all seven security controls actually enforced in your SIP flow?
Wrapping Up
Improving SIP security isn’t just about stopping obvious attacks, it’s about preventing small signaling issues from turning into outages, abuse, or revenue loss. For VoIP providers, SIP sits at the core of service reliability, and gaps at this layer tend to surface when traffic scales or behavior changes.
🗝️ Key Takeaways
- SIP security problems often come from subtle signaling patterns, not loud attacks.
- OpenSIPS modules provide behavior-level control that complements SBCs and network defenses.
- A layered approach, combining modules, monitoring, and integration, is what keeps SIP platforms stable in production.
Hardening SIP security takes more than enabling modules; it requires understanding how they interact with real traffic. This is where working with Hire VoIP developer helps, from auditing existing OpenSIPS deployments to designing signaling logic that scales securely as your platform grows.


