📝 Blog Summary
Modern OpenSIPS WebRTC integration eliminates browser compatibility headaches while maintaining carrier-grade call quality. This guide covers proven WebRTC integration techniques, security configurations, and performance optimizations that actually work in production environments.
Your users expect seamless browser-based calling without plugins, but most WebRTC integration attempts crash under load or fail security audits. The challenge isn’t just connecting browsers to SIP networks; it’s building a system that handles thousands of concurrent connections while maintaining call quality and security standards.
OpenSIPS WebRTC integration solves this by providing a robust SIP proxy layer that translates between WebRTC’s requirements and traditional telephony infrastructure. Unlike basic WebRTC gateways that handle simple protocol conversion, OpenSIPS offers advanced routing logic, load balancing, and security features that enterprise communications actually need.
Understanding OpenSIPS WebRTC Architecture
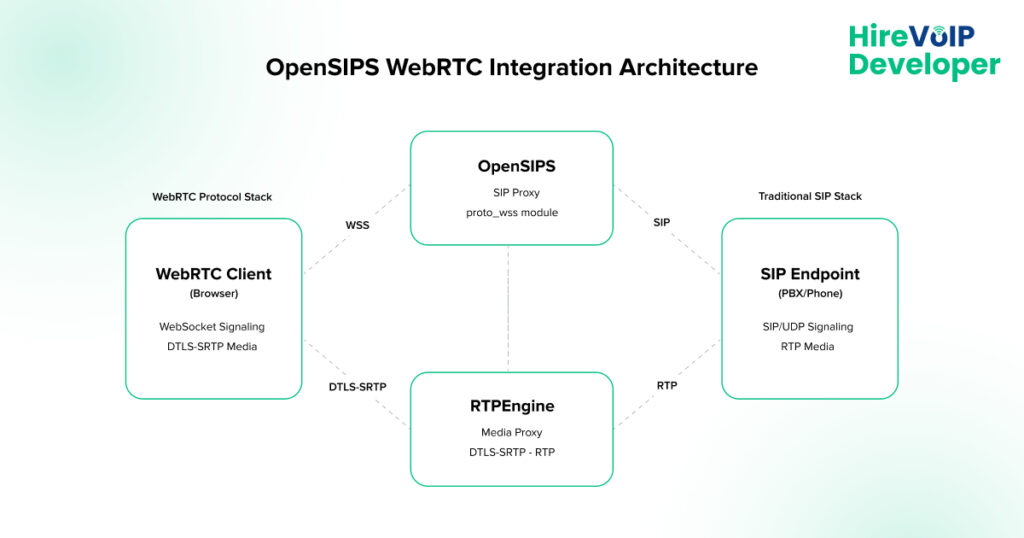
The foundation of successful WebRTC integration lies in understanding how OpenSIPS bridges the gap between browser-based WebRTC clients and traditional SIP infrastructure. OpenSIPS functions as both a WebSocket server for browser connections and a SIP proxy for backend telephony systems.
OpenSIPS for Real-Time WebRTC Communication requires three core components working in harmony:
- WebSocket Transport Layer: Handles browser connections using secure WebSocket (WSS) protocols, managing persistent connections and protocol translation between browsers and SIP infrastructure.
- SIP Proxy Core: Manages call routing, authentication, and session management while coordinating between different transport mechanisms and maintaining session state.
- Media Handling Component: Coordinates RTP streams between WebRTC endpoints and traditional SIP devices, handling encryption requirements and codec negotiation.
The architecture differs fundamentally from standard SIP proxy deployments because WebRTC introduces additional complexity around media negotiation, security requirements, and connection management. Browsers can’t directly connect to UDP-based SIP servers, so OpenSIPS must translate WebSocket messages to SIP protocols while maintaining session state across different transport mechanisms.
OpenSIPS handles this translation through specialized modules that convert WebRTC’s mandatory encryption requirements into formats compatible with existing PBX systems. The system manages DTLS-SRTP for media encryption, handles ICE connectivity checks for NAT traversal, and coordinates codec negotiation between WebRTC’s limited codec support and traditional telephony equipment.
Also read: OpenSIPS 3.6 New Features Explained
Essential OpenSIPS Modules for WebRTC Integration
Successful WebRTC integration depends on configuring the right combination of OpenSIPS modules, each handling specific aspects of the WebRTC communication stack.
Core WebRTC Modules
- proto_wss: Provides WebSocket transport support, enabling browsers to establish persistent connections with the OpenSIPS proxy.
- nathelper & rtpengine: These work together to handle media relay and NAT traversal challenges inherent in WebRTC deployments, coordinating RTP stream processing and STUN/TURN server integration.
- auth_db & permissions: Validate WebRTC client credentials and enforce access controls with browser-compatible authentication mechanisms.
Security and Session Management
- tls_mgm: Manages SSL/TLS certificate handling for secure WebSocket connections, ensuring encrypted signaling paths meet WebRTC security requirements.
- dialog: Tracks active sessions, handles connection recovery, and manages cleanup when WebRTC clients disconnect abruptly to prevent resource leaks.
- registrar & usrloc: Handle WebRTC client registration with dynamic contact management that accounts for changing network conditions.
Your WebRTC calls work in testing but fail in production? We've solved this MANY times!
How to Integrate WebRTC and OpenSIPS? Step-by-Step Implementation
The WebRTC OpenSIPS implementation process follows a systematic approach that builds WebRTC capability on top of existing OpenSIPS infrastructure.
1. Transport Configuration
Configure WebSocket transport by adding listen directives for both WebSocket and secure WebSocket protocols in opensips.cfg.
The configuration should specify appropriate TLS certificates and handle both IPv4 and IPv6 connections. Most production deployments require load balancer integration, so your configuration must account for proxy protocol headers and connection persistence.
2. Database Schema Preparation
Extend standard OpenSIPS tables to support WebRTC-specific attributes. The subscriber table needs fields for WebRTC capability flags, codec preferences, and security certificates.
The location table requires modifications to handle WebSocket connection persistence and browser-specific contact information.
3. Routing Logic Implementation
Your script must detect WebRTC clients based on contact headers, apply appropriate media handling for browser connections, and coordinate between WebSocket and UDP transport protocols.
The routing script needs separate handling paths for:
- WebRTC-to-WebRTC calls with optimized media paths
- WebRTC-to-PSTN calls requiring codec transcoding
- Traditional SIP-to-WebRTC incoming call delivery
4. Media Relay Configuration
Configure RTPEngine with specific WebRTC optimization parameters that handle DTLS-SRTP encryption, coordinate ICE candidate exchange, and manage codec transcoding between WebRTC’s limited codec support and carrier requirements.
Advanced OpenSIPS WebRTC Configuration Techniques
Once you’ve got basic WebRTC integration working, the real engineering work begins. Enterprise deployments demand features that aren’t covered in tutorials: clustering that actually maintains session state, performance tuning that handles WebSocket connection patterns, and security hardening that addresses WebRTC-specific attack vectors.
High-Availability and Clustering Setup
High-availability deployments require an OpenSIPS clustering configuration that maintains WebRTC session state across multiple proxy instances. The clusterer module enables state replication between OpenSIPS nodes, ensuring WebRTC calls survive individual server failures without interrupting active sessions.
Database replication strategies must account for the high-frequency updates generated by WebRTC client registrations and connection state changes. Consider implementing database connection pooling and read/write splitting that can handle the increased database load generated by persistent WebSocket connections.
Performance Tuning for WebRTC Workloads
Performance tuning involves optimizing OpenSIPS for the different resource utilization patterns created by WebRTC clients. WebSocket connections consume more memory per client than traditional SIP registrations, requiring adjusted memory limits and connection handling parameters.
Configure TCP connection timeouts and cleanup intervals that balance resource usage with connection reliability.
External Service Integration
Integration with external services often requires custom routing logic that coordinates between WebRTC clients and traditional telephony infrastructure.
Your OpenSIPS configuration might need integration with CRM systems, call center platforms, or billing systems that weren’t designed for WebRTC’s connection characteristics.
Production Security Hardening
Security hardening for production WebRTC deployments involves implementing rate limiting that prevents WebSocket connection flooding, configuring intrusion detection that recognizes WebRTC-specific attack patterns, and maintaining certificate management processes that handle the increased certificate usage in WebRTC-enabled systems.
WebRTC SIP Integration Best Practices
Getting WebRTC clients to register and make calls is one thing. Building a system that handles real-world network conditions, security threats, and enterprise-scale requirements is entirely different.
These best practices separate proof-of-concept deployments from production-ready systems.
Security Implementation
Security goes beyond basic TLS encryption because WebRTC introduces unique attack vectors not present in traditional SIP deployments:
- Origin Validation: Validate origin headers to prevent cross-site scripting attacks and implement proper CORS (Cross-Origin Resource Sharing) policies for browser compatibility.
- Certificate Management: Handle certificate validation for encrypted media streams and maintain certificate renewal processes for WebSocket connections.
- Authentication Adaptation: Implement token-based authentication or OAuth integration that works seamlessly with browser security models.
Network Topology and Performance
- STUN/TURN Coordination: Your OpenSIPS deployment must coordinate with STUN/TURN servers for NAT traversal and handle mobile network transitions gracefully.
- Connection Quality Monitoring: Implement monitoring that can trigger media path changes when network conditions degrade.
- Load Balancing Strategy: Configure session affinity while providing failover capabilities, with health checks that account for WebSocket connection health rather than just SIP registration status.
Codec Management
Handle codec negotiation between Opus/G.722 from browsers and G.711/G.729 from PSTN gateways. This often requires transcoding capabilities that maintain audio quality while minimizing latency introduced by codec conversion.
Media Handling and Optimization in WebRTC OpenSIPS Integration
Here’s where most WebRTC projects hit the wall. You’ve got browsers connecting, calls are establishing, but the audio quality is inconsistent, users complain about delays, and high-bandwidth connections are choking your network. The difference between a working demo and production-grade WebRTC lies in media path optimization.
RTPEngine Configuration for WebRTC
Media path optimization represents the difference between acceptable call quality and production-ready performance in WebRTC VoIP Setup with OpenSIPS. The system must minimize latency while handling the encryption requirements and codec limitations inherent in WebRTC communications.
RTPEngine configuration for WebRTC requires specific optimization flags that handle browser audio processing characteristics.
- Enable WebRTC-specific jitter buffer management
- Configure appropriate packet loss concealment algorithms
- Implement dynamic codec switching based on network conditions.
💡 Our Experts Suggest
Most WebRTC performance issues stem from improper RTPEngine flags rather than network problems. Always enable ICE=force and DTLS=passive for browser clients, but use DTLS=active for mobile WebRTC apps. This single configuration difference prevents many of the media connectivity failures we see in production deployments.
Audio Quality Management
Audio quality optimization involves configuring OpenSIPS to work with WebRTC’s automatic gain control, noise suppression, and echo cancellation features. Your system should coordinate these browser-native audio processing features with network-level optimizations to prevent conflicts that degrade call quality.
Bandwidth Control and Adaptive Quality
Bandwidth management becomes crucial in WebRTC deployments because browsers may attempt to use high-bandwidth codecs inappropriate for network conditions.
- Implement codec preference enforcement that matches network capabilities
- Configure adaptive bitrate mechanisms that respond to changing conditions
- Provide quality degradation paths that maintain call connectivity when bandwidth becomes constrained
WebRTC-Specific Monitoring
Monitoring and diagnostics require WebRTC-specific metrics beyond traditional SIP monitoring. Your monitoring system should correlate network-level metrics with application-level call quality indicators.
- Track WebSocket connection stability
- Monitor DTLS handshake success rates
- Implement call quality measurements that account for browser-specific audio processing
Troubleshooting Common OpenSIPS WebRTC Integration Issues
WebRTC troubleshooting is fundamentally different from traditional SIP debugging. You’re dealing with browser-specific behaviors, encrypted media paths, and connection types that change mid-call. The usual SIP debugging approaches miss the WebRTC-specific failure points that cause the most production headaches.
Here are some common WebRTC integration issues and solutions:
WebSocket Connection Failures
- Certificate Problems: Verify TLS certificates include appropriate subject alternative names for your WebRTC domain.
- Firewall Restrictions: Ensure firewall rules allow WebSocket traffic on configured ports and check load balancer WebSocket upgrade header handling
- Connection Persistence: Configure appropriate timeout values for WebSocket connections in high-latency environments
Media Connectivity Issues
- STUN/TURN Configuration: Debug media path establishment by examining ICE candidate exchange logs and verifying TURN server credentials
- RTPEngine Integration: Confirm RTPEngine receives proper WebRTC-specific flags for media processing and encryption handling
- NAT Traversal: Verify STUN server network reachability and ICE connectivity check success rates
Authentication and Call Quality Problems
- Origin Validation: Implement comprehensive logging for authentication attempts and verify CORS header configuration for cross-origin requests
- Media Path Analysis: Monitor codec negotiation logs, track RTP packet loss and jitter statistics, and correlate call quality reports with network performance metrics
- Browser Compatibility: Ensure authentication tokens remain valid across WebSocket connection reconnections and handle browser-specific audio processing variations
🚀 Ready to Future-Proof Your VoIP System with OpenSIPS + WebRTC?
When to Consider Expert Implementation?
When complexity exceeds internal capabilities or timeline pressures demand faster deployment, consider the option to hire OpenSIPs developers with proven WebRTC integration experience.
Specialized expertise can accelerate deployment timelines, avoid common implementation pitfalls, and ensure your system meets enterprise performance requirements from day one. The techniques we’ve covered here represent tested approaches that work in production environments, but the most important thing to take away?
Implementation success depends on careful attention to the security, performance, and scalability considerations that separate functional demos from enterprise-ready systems.
If you’re serious about performance, scale, and reliability, it pays to bring in engineers who know what breaks and why. For high-scale, low-latency WebRTC development with OpenSIPS integration, connect with us!


